ETFMG Prime Cyber Security ETF (HACK)
Key Statistics
Minor Support Level 51.52 Minor Resistance Level 59.26
Major Support Level 28.38 Major Resistance Level 64.36
Minor Buy Signal 62.55 Minor Sell Signal 48.69
Major Buy Signal 72.93 Major Sell Signal 22.38
BRIEF OVERVIEW – HACK ETF
Without question, one of the fastest growing industries on a global basis is the cybersecurity industry. In 2004, the industry was valued at a paltry $3.5 billion. By the end of 2019, spending on global cybersecurity had exploded to $124 billion. This represents an increase of 3,443% over the course of the past 15 years. No other major industry even comes close to matching this type of growth rate. Based on data provided by Gartner Inc, cybersecurity spending is projected to reach $170.4 billion by 2022. There appears to be no end in sight.
What exactly is cybersecurity and why has the industry increased so dramatically during the past decade? Cybersecurity is the protection of computer systems from the theft and damage to their hardware, software or information. It also protects from the disruption of services they provide. The industry is growing so dramatically due to the increasing reliance on computer systems and the internet. This would include such things as wireless networks (i.e. Bluetooth and Wi-Fi) as well as “smart” devices like smartphones smartwatches, smart cars and various types of smart consumer electronic devices.
In an effort to provide investors with exposure to the cybersecurity industry, the ETFMG family of exchange traded funds launched the Prime Cyber Security ETF on 12 November 2014. The ticker symbol is HACK. This investment product is the world’s first ETF focused on the cybersecurity industry. More specifically, HACK is comprised of companies that offer hardware, software and consulting services designed to defend against cybercrime. The ETF includes 57 different holdings. The top five holdings are Cisco Systems, BlackBerry Limited, Fortinet Inc, Palo Alto Networks Inc and Commvault Systems Inc.
SHORT-TERM VIEW
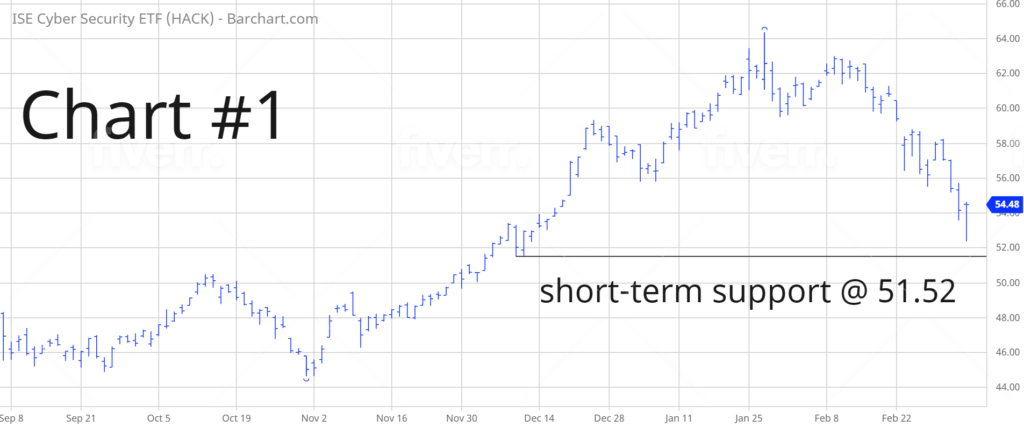
HACK enjoyed a substantial rally following the pandemic low in March 2020. The ETF advanced 121.8% over the course of nine months. HACK formed a top on 27 January @ 64.36. During the past six weeks, HACK has generated a rather sharp decline of 15.3%. The short-term momentum has flipped from bullish to bearish. The next level of support is 51.52. The bulls need a close above 59.26 in order to reclaim the momentum on a short-term basis. The most likely scenario is a trading range for the next several weeks.
Based on the Aroon Oscillator, HACK has an oversold reading of -68. The Aroon Oscillator is programmed differently than most stochastic indicators. The oscillator fluctuates between -100 and +100. A reading of 0 would indicate a neutral position. Therefore, a reading of -68 with HACK is considered fairy oversold. The ETF is probably in store for a short-term bounce.
LONG-TERM VIEW
In many respects, the cybersecurity industry is still in its infancy stage. In fact, the industry didn’t even exist until the internet became a part of our daily lives beginning in the mid-1990s. These days, companies are spending huge amounts of money on cybersecurity in order to prevent computer viruses and the theft of personal data. Let’s review a few of the industries with the largest cybersecurity budgets.
In terms of cybersecurity vulnerability, the financial services industry has the potential to suffer the greatest loss. These losses could occur from a financial standpoint as well as customers losing faith in the products and services.
Hackers are constantly targeting financial regulators and financial institutions in an effort to manipulate the markets and generate illicit gains. The financial regulators most at risk include the Securities and Exchange Commission, the Federal Reserve and the SWIFT network. In regard to financial institutions, commercial banks, brokerage firms, investment banks and credit card companies pose the greatest amount of risk to individual consumers. Additionally, any website or smartphone app that stores sensitive financial information would be a prominent hacking target.
The utilities industry is another area of major concern by cybersecurity experts. Technology has completely altered the way businesses and consumers receive utility services. During the past two decades, computers have played an ever increasing role in controlling the functions at most utility companies. This includes the coordination of telecommunications, the power grid, nuclear power plants as well as valve openings and closings in water and gas networks. Any type of cyberattack in the utilities industry would cause major disruptions to our way of life.
The aviation industry is also vulnerable to cyberattacks. The industry uses a series of complex systems in order to operate on a daily basis. A simple power outage at one airport can cause repercussions on a worldwide basis. Much of the aviation industry relies on radio transmissions, which can easily be disrupted by a cyberattack. An additional source of vulnerability is the safety of aircrafts over ocean waters. Radar surveillance only extends 200 miles offshore. Therefore, the aviation industry must be constantly on guard against even the slightest cyber threat.
In addition to financial institutions, large corporations are common targets of cyberattacks. The most common type of cyberattack involves identity theft and the breach of personal data. An example would include the loss of customer credit card numbers. During the past few years, several corporations became victims of credit card theft. The most prominent names were Home Depot, Staples and Target Corporation. Of course, the greatest security breach on record belongs to Equifax, where a total of 150 million customer profiles were reported stolen in September 2017. Most likely, cyberattacks will continue to increase against large corporations based on the fact that these firms control such large amounts of personal data.
As you can see, there exists an enormous amount of vulnerabilities throughout the domestic economy. This explains why the cybersecurity industry will continue to enjoy double digit growth rates well into the next decade. Most likely, artificial intelligence (AI) will play an important role in reducing the number of cyberattacks throughout the global economy. However, AI is a relatively new concept, particularly in terms of its application in preventing cybercrimes. Therefore, the cybersecurity industry will continue to be a major revenue generator for the next several years.
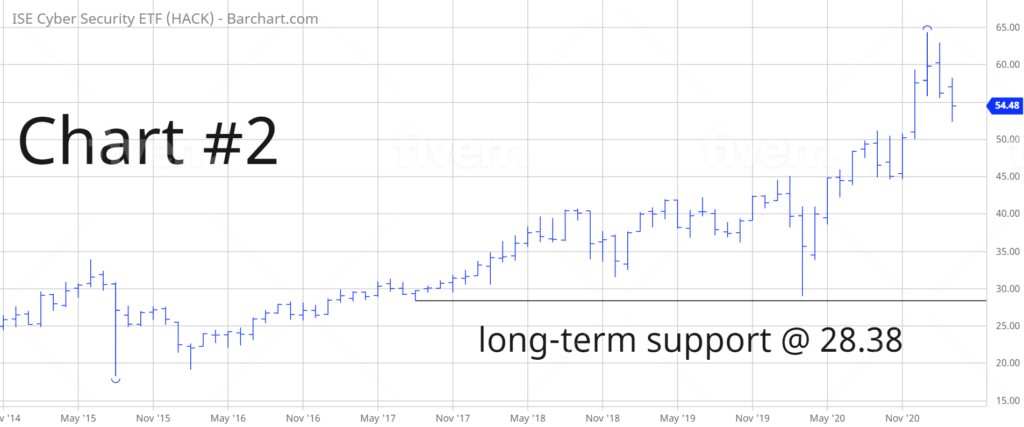
The long-term view of HACK remains quite bullish. Of course, the ETF has only been in existence for six years. Therefore, HACK has a limited amount of historical data. Nevertheless, the bulls have been in complete control of HACK for the past five years. With the exception of the brief bear market in March 2020, the ETF has basically gone straight up since February 2016. The next level of resistance is the all-time high from 27 January @ 64.36. The bears need a weekly close below 28.38 in order to recapture the downside momentum.
SHORT-TERM TREND – HACK ETF
Please review the 6-month chart of HACK (Chart #1). The short-term chart pattern remains bearish. The next level of support is 51.52. A weekly close above 59.26 will turn the chart pattern in favor of the bulls. The most likely scenario is a trading range for the next few months.
LONG-TERM TREND
Please review the 6-year chart of HACK. This chart contains the entire trading history of HACK. Therefore, it’s rather difficult to generate a long-term forecast. However, based on the current price data, the bulls are in complete control of HACK. The ETF has enjoyed a continuous grind to the upside since February 2016. Currently, there’s no indication to expect a bear market reversal any time in the near future.
How To Avoid Becoming The Victim Of A Cyber-Attack
Contrary to popular belief, the biggest threat to your personal financial security is not a global economic meltdown or a hyperinflationary collapse of the US Dollar. Admittedly, these financial events would certainly be quite painful. However, the overall risk of such an event is rather small. Instead, the most likely threat to your financial well-being is a cyber-attack. During the past decade, attacks on personal information and theft of private financial data has exploded to epic proportions. This includes such things as:
- credit card theft
- identity theft
- hackers filing a false tax return using your SSN
- cyber thieves applying for a bank loan in your name
- cyber thieves applying for a credit card in your name
- attackers taking control of your cell phone through “SIM swap”
- theft of cryptocurrency wallets
- using spyware to gain control of your computer keyboard
- using spyware to gain control of your cell phone keypad
- hackers stealing your PIN number, password and user ID
- cyber thieves installing malicious software on your computer or notebook
- cyber thieves installing malicious software on your cell phone
Theft of personal information should be considered a national security issue. However, the financial services industry and the retail industry have absolutely no desire to shine a light on this problem. Why? Because these institutions want you to believe that your money and your personal information are 100% safe. This is simply not true. Banks, brokerage firms, credit card companies, lending institutions, major retail companies and social media websites are completely unable and unprepared to safeguard your personal information. These institutions are fighting a losing battle. If you’re relying on these institutions to protect your personal data and financial information, you will be hugely disappointed.
Based on data provided by Cybersecurity Ventures, cybercrime will cost global consumers $6 trillion in 2021. This number will increase to $10.5 trillion by 2025. Every 24 hours, $16.4 billion is lost to cybercrime. This number includes: theft of personal data, theft of financial data, embezzlement, fraud, theft of intellectual property and restoration of lost data.
Cybersecurity experts agree that cyber-attacks are so prevalent in today’s global economy, that you should expect to be a cyber theft victim at some point in your life. In fact, the probability that your personal information is floating around on the dark web is near 100%. What is the dark web? It is part of the World Wide Web where cyber thieves and hackers obtain personal information on consumers and businesses. This information includes such things as social security number, date of birth, cell phone number, address, place of birth, mother’s maiden name, employment information, credit card numbers, bank account numbers and email address. This is just a partial list of items that are available on the dark web. Again, you should assume with 100% certainty that your personal and financial information is currently for sale on the dark web.
How To Minimize A Cyber-Attack
The only way to reduce your chances of becoming the victim of a cyber-attack is through education and prevention. The biggest mistake you can make is to simply pretend that this problem doesn’t exist or that you are immune from becoming the victim of cyber theft. Unfortunately, all of the prevention in the world will not completely safeguard you from falling prey to a cyber thief. However, it’s much better than ignoring the problem.
What can you do to minimize the risk of a cyber-attack? Let’s review a list of simple things you can do to keep hackers and cyber criminals away from your personal data.
Strengthen your passwords – These days, most websites require a user ID and password. This is particularly true of financial websites and other websites that contain personal information. The biggest mistake you can make is to use short passwords or passwords that contain common names and phrases. The best password is a mixture of uncommon letters, numbers and symbols. For example: FGM863*hza Each password should be a minimum of ten characters.
Change your passwords – You should change each password a minimum of four times per year.
Use multiple passwords – Use a different password for each website. Never use the same password for multiple websites.
Store your passwords on a sheet of paper – Many people make the mistake of storing their passwords on a personal computer, notebook, laptop or cell phone. This is not a good idea because all of these devices can easily be stolen or hacked. The best solution is to write your passwords on a single sheet of paper. Another solution is to save passwords on a USB drive. However, don’t allow the USB drive to remain attached to your computer.
Google Chrome – Most people are unaware that Google offers a number of useful resources to help users manage their passwords. Google Chrome can tell you if your passwords have been compromised or if your passwords are likely to be hacked. All of this data is available by accessing the Google Chrome control panel under “settings.”
Credit Freeze – One of the most popular forms of cyber theft is applying for a credit card or bank loan using a stolen social security number (SSN). It’s incredibly easy for a thief to obtain a credit card in your name using your SSN. Fortunately, it’s very easy to prevent this type of cyber theft. The solution is to lock down your credit profile with each of the major credit bureaus. This service is available free of charge and it completely prevents a thief from applying for credit in your name.
Lock your credit cards – If you don’t use your credit card on a daily basis, the best course of action is to lock the card. If your credit card number is stolen, it’s impossible for a thief to use a locked credit card. These days, all of the major credit card companies allow users to lock their cards by visiting the company website. It’s very easy to lock and unlock a credit card.
Use two cell phones – The most painful cyber-attack involves the theft of your cell phone through a method known as SIM swap fraud. Are you familiar with a SIM card? If not, a SIM card is a plastic chip located inside your cell phone. It tells your mobile device which cellular network to communicate with. SIM swap fraud occurs when a cyber thief contacts your cell phone provider and convinces the customer service representative (CSR) to delete the SIM card linked to your phone and replacing it with a new SIM card owned by the cyber thief. Upon switching the SIM card, the thief immediately has complete access to your cell phone. If your cell phone mysteriously quits working, you probably have been the victim of SIM swap fraud. Unfortunately, SIM swap fraud is exploding in popularity within the cyber theft community.
Many people are absolutely amazed that the major network providers (i.e. AT&T and Verizon) allow SIM swap fraud to occur so easily. The vast majority of cell phone customers are under the illusion that their data is safe and secure. Nothing could be further from the truth. In fact, your cell phone (and accompanying cell phone data) is incredibly vulnerable to cyber-attack. The “weak link” occurs between the network provider and its CSRs. In terms of AT&T, the majority of employees who work in customer service call centers are located in poor countries such as Mexico, Philippines, Vietnam and Bangladesh. During the past 10+ years, AT&T has closed most of its call centers in the United States, and moved 12,000 jobs to poorly developed countries with low wages. Of course, AT&T is saving a ton of money on employee wages. However, the quality of the company’s customer service has collapsed.
Unfortunately, many of the CSRs can barely speak English. Therefore, it’s very easy for these “smooth talking” cyber thieves to convince the CSR to switch the cell phone SIM card. Additionally, many hackers will boldly offer a “cash bonus” to these poorly paid workers in exchange for performing a SIM swap. It’s not uncommon for CSRs to make more money by accepting bribes from hackers and thieves than they make in their weekly salary from AT&T. Hopefully, now you understand that your cell phone data is incredibly vulnerable to SIM swap fraud. In fact, you should absolutely expect your cell phone to be hacked at some point in your life. This problem will never disappear. It will only get worse.
A great way to minimize the damage of a cell phone attack is to purchase an additional cell phone. My suggestion is to obtain a low-cost smart phone with minimal features and a basic monthly data plan. Do not select AT&T or Verizon as your carrier. Instead, use a network provider with call centers located in the United States. My suggestion is the Jitterbug smart phone issued by GreatCall. The cost of the phone is less than $200. The monthly data package is approximately $20. Most importantly, all customer service call centers are located in the United States.
A good plan of action is to transfer all of your financial accounts to the Jitterbug phone. These days, most cell phone users have financial apps linked to their smart phone. This would include such things as credit card accounts, bank accounts, brokerage accounts, investment accounts, Bitcoin digital wallets and mobile pay apps like Venmo and PayPal. All of these financial apps should be removed from your primary cell phone and added to the new Jitterbug phone. If your primary cell phone ever suffers a SIM swap hack, the cyber thief will be unable to access any of your financial information. Why? Because all of your important financial data will be safely stored on the Jitterbug phone.
Another suggestion is to carefully guard your new Jitterbug phone number. Don’t share the phone number with anyone. Obviously, SIM swap fraud is impossible unless the hacker has your cell phone number. Therefore, it’s always best to maintain the privacy of your new Jitterbug phone number. Also, keep your Jitterbug phone at home. Don’t travel with the new phone and don’t use it for day-to-day operations. Instead, use your primary smart phone for texting, chatting, watching videos and visiting websites.
Create a password with your cell phone provider – One of the best ways to minimize the risk of SIM swap fraud is to establish a telephone password with your cellular network. A telephone password acts as a “security wall” between you and the CSR. If a cyber thief attempts to contact your cellular provider, they will be unable to access your account information unless they know your telephone password. Do you have a telephone password with your cell phone company? If not, you’re missing a golden opportunity to easily minimize the risk of SIM swap fraud.
Don’t open unknown email attachments – One of the easiest ways for a cyber thief to gain access to your personal information is by installing malware on your computer or mobile device. Malware is installed when you inadvertently open an infected email attachment. Once the malware has been installed, the damage is done. A simple way to prevent malware is never open an email attachment from an unknown sender.
Install anti-virus software – These days, most new computers have an anti-virus software pre-installed. These programs run in the background while you work on the computer. Anti-virus software is certainly not perfect. However, it’s better than nothing. Please check your computer for an anti-virus application. The most popular anti-virus package is probably McAfee or Norton.
Place digital currencies in cold storage – Do you own cryptocurrencies like Bitcoin or Ethereum? If so, you should seriously consider removing these digital assets from mobile wallets, web wallets and desktop wallets. These types of storage devices are known as “hot wallets” because they are linked to the internet. Consequently, hackers have access to these digital currencies. In fact, any cryptocurrency attached to a website or mobile app is highly vulnerable to theft. There’s absolutely no justifiable reason why Bitcoin owners should store their crypto in a hot wallet. You’re asking for trouble. All digital currencies should be removed from hot wallets and placed in cold storage. The most popular cold storage devices are Ledger Nano X and YubiKey.
Final Thoughts
It’s impossible to completely eliminate cyber-attacks. However, you can substantially reduce the likelihood of becoming the victim of a hacker. If you will devote a few hours to putting the proper procedures in place, you could potentially save yourself months of emotional pain, aggravation, misery and loss of money. Unfortunately, most people who read this report will not take any action because they don’t want to go through the trouble of taking the necessary steps to prevent a cyber-attack. Also, many people believe that cyber-attacks won’t happen to them. If you feel as though you are immune from an attack, you are wrong. In fact, the number of cyber-attacks have exploded in response to the global pandemic. This problem will only get worse because we all spend an ever-increasing amount of our time connected to a personal computer or mobile device. Don’t allow yourself to become the victim of an attack.